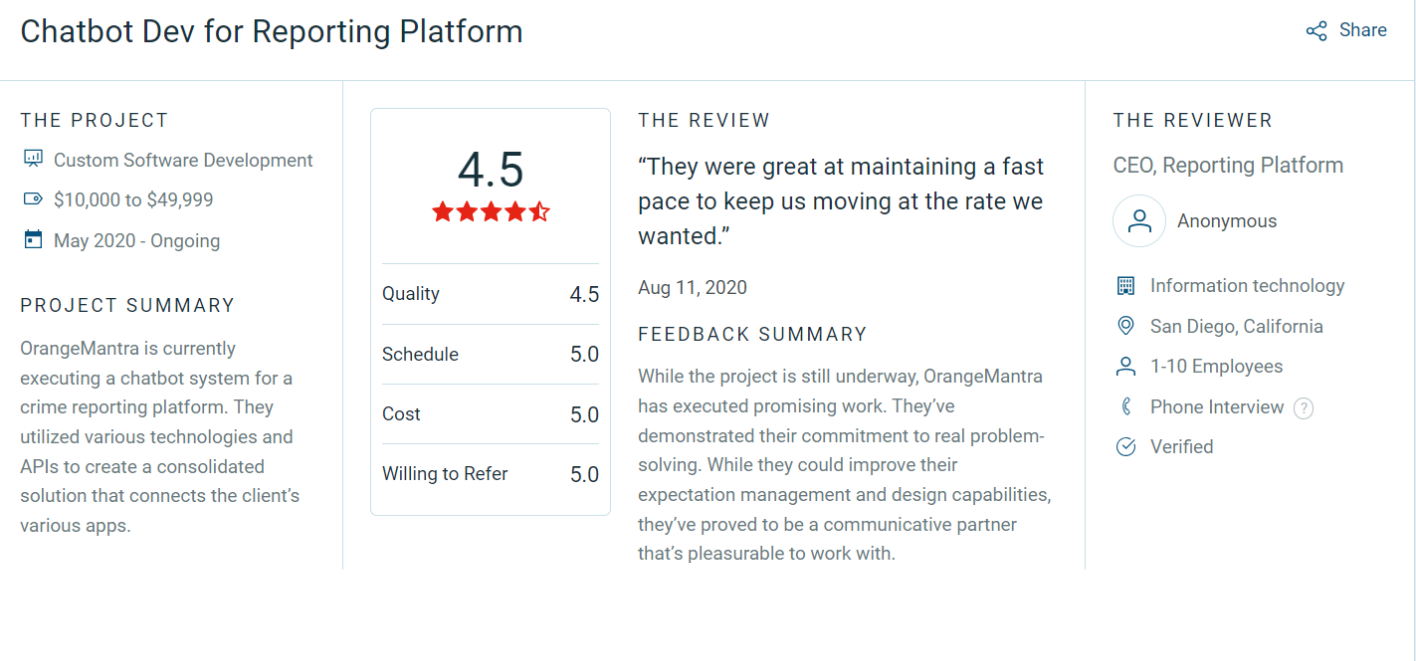
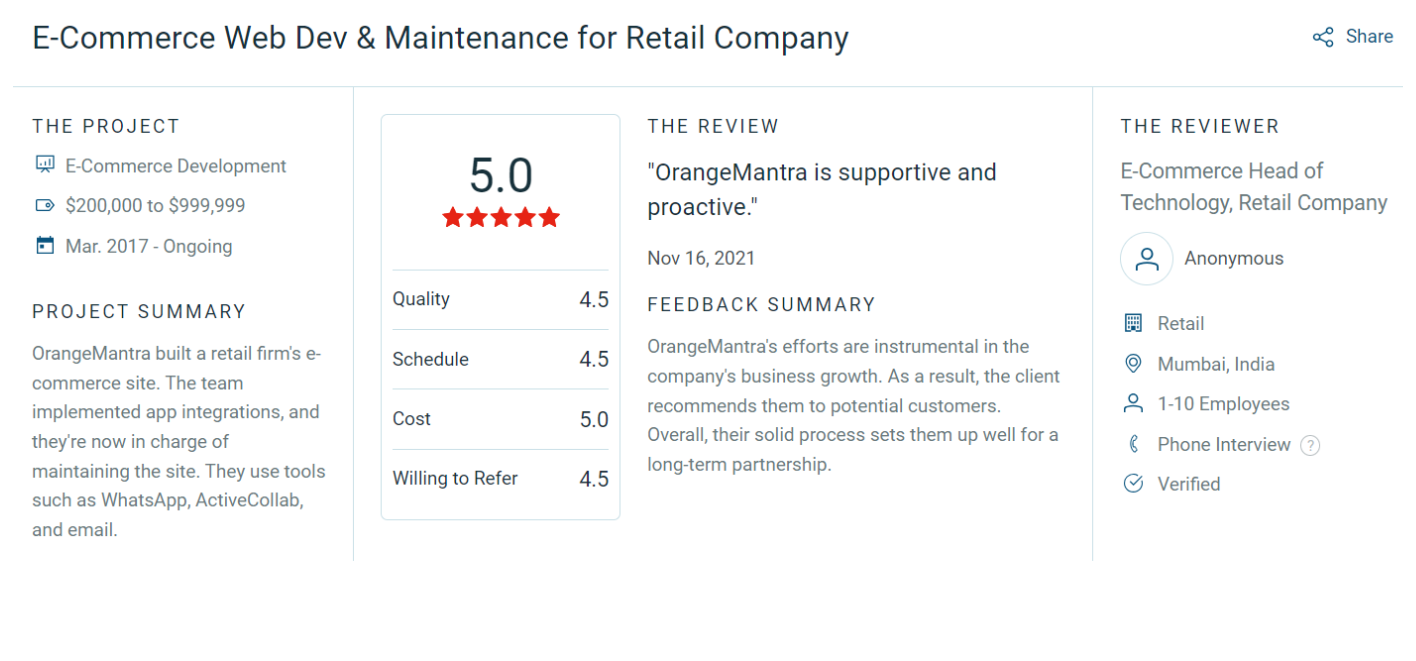
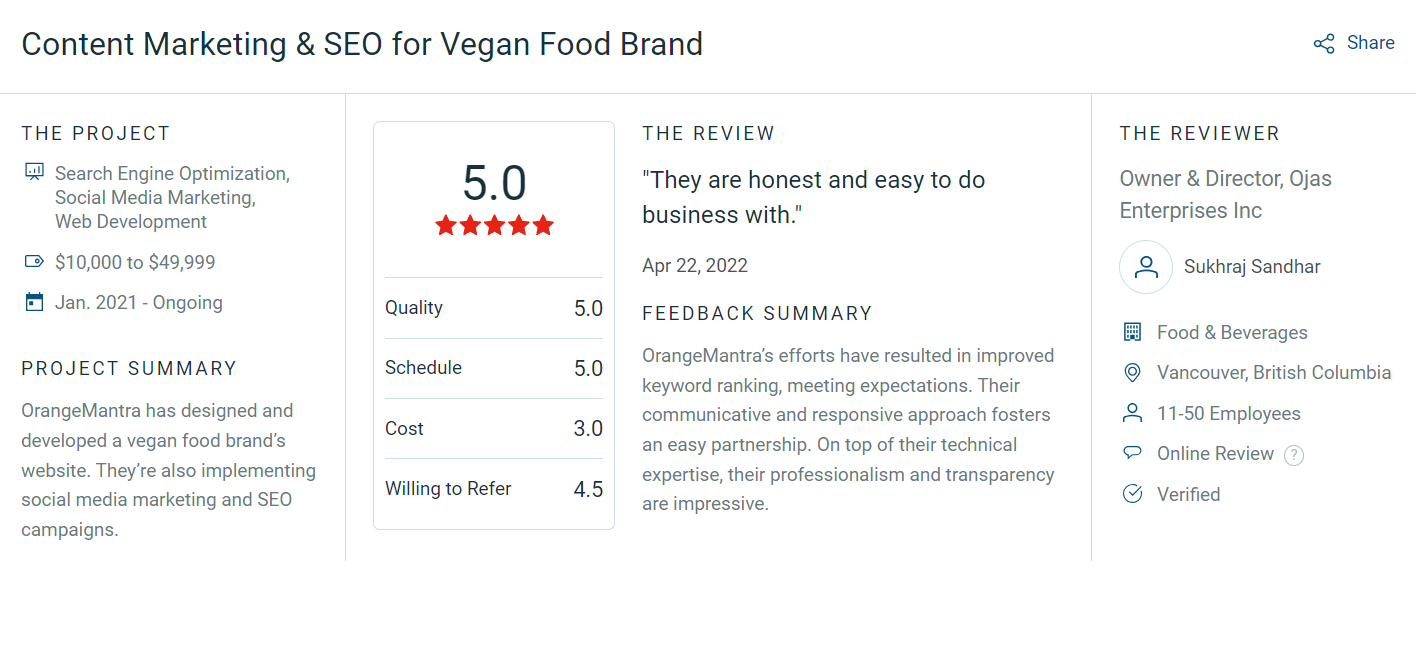
The Problem
As a recognized brand, our client has developed an IoT-based mobile app for their passenger cars. But being operated in online mode, the connected cars is vulnerable to hacks. Our client searched for a reliable security partner to ensure driver safety and privacy. They need a series of security assessments and penetration tests on their connected car app.