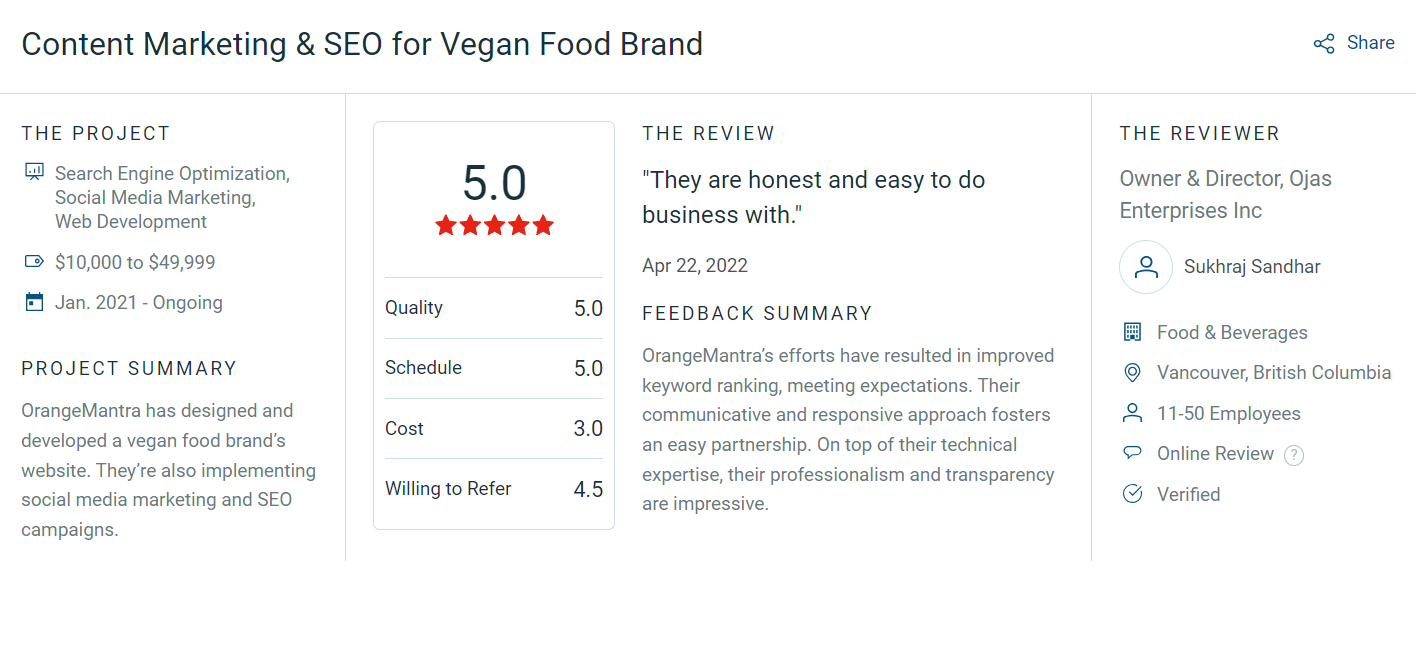
Leading VAPT Testing Services for seamless testing solutions
Secure applications from cyberattacks with end-to-end vulnerability assessment with VAPT services.
Business-focused Services
Streamlined Penetration Testing
Proactive Threat Solutions
Unparallel Security Measures
Extensive 24/7 Support




















 Python
Python  JavaScript
JavaScript Golang
Golang Java
Java Flask
Flask React.js
React.js Spring Boot
Spring Boot Express.js
Express.js Terraform
Terraform Docker
Docker Kubernetes
Kubernetes  Cloud Build
Cloud Build Cloud Firestore
Cloud Firestore  Cloud SQL
Cloud SQL BigQuery
BigQuery MongoDB Atlas
MongoDB Atlas